Third-Party Security
Monitoring Software
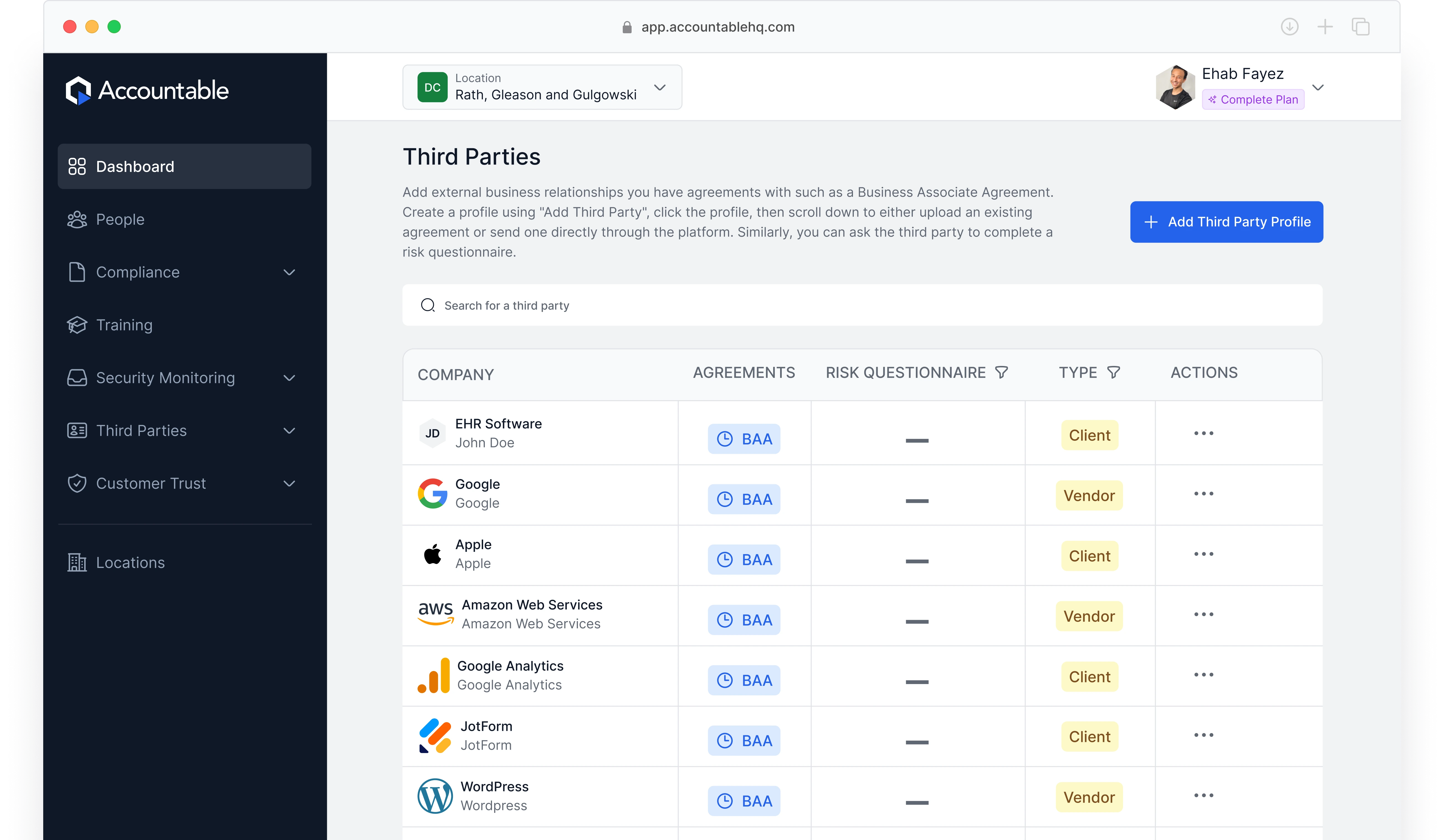
In today's digital landscape, businesses rely on third-party services like Google, Apple, Slack, and HubSpot to operate efficiently. However, these external relationships also introduce security risks that must be monitored. Accountable's Third-Party Security Monitoring feature helps you track and manage the compliance status of your vendors, partners, and service providers, ensuring data security and regulatory adherence.






-
Why Is Third-Party Security Monitoring Important?
External businesses handling your Protected Health Information (PHI) or other sensitive data can pose significant security risks. Continuous monitoring of these partners helps organizations maintain control and compliance.
-
Identify potential vulnerabilities before they become security threats
-
Ensure third parties comply with regulatory standards like HIPAA, GDPR, and CCPA
-
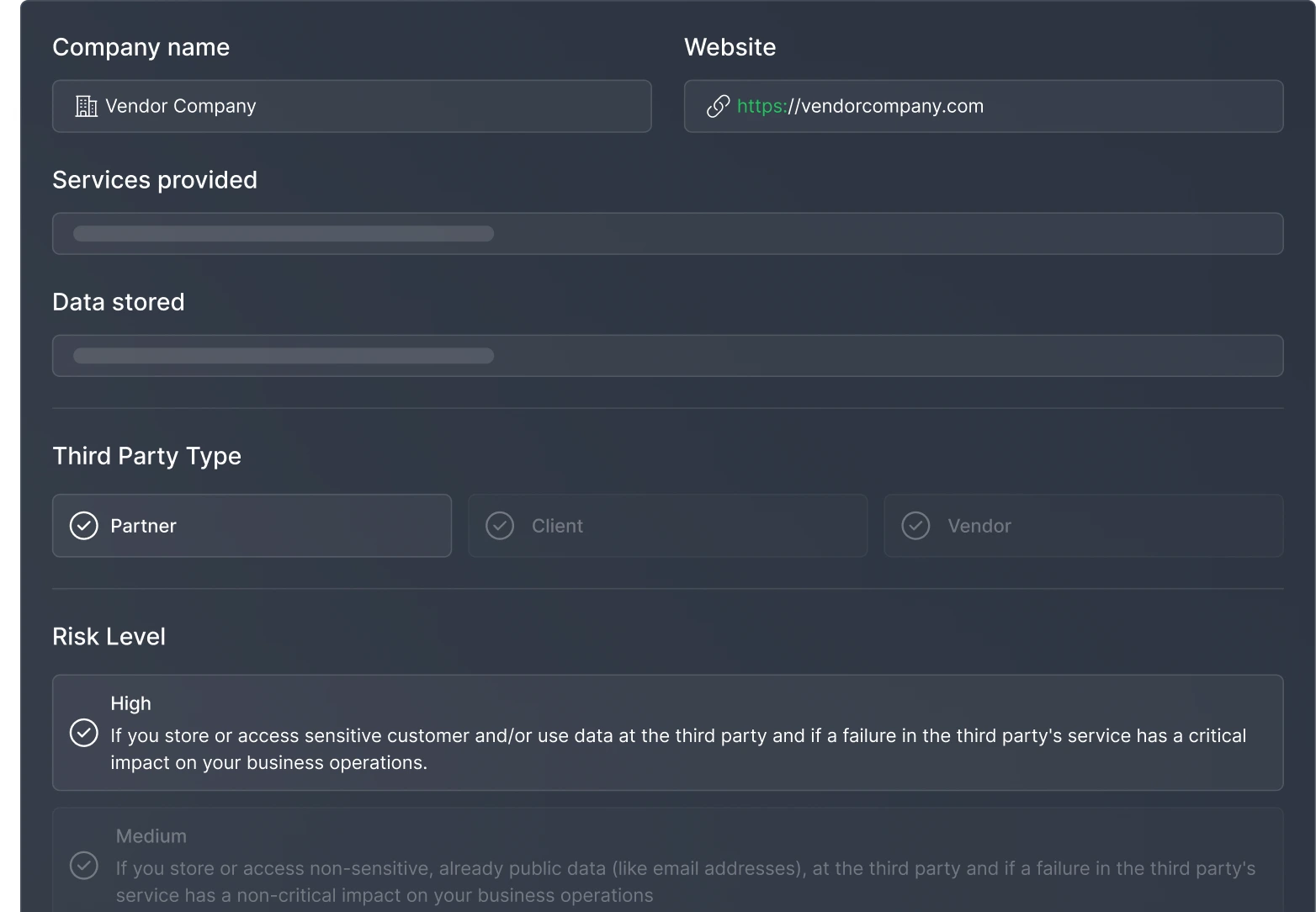
Maintain control over vendor security through agreements and risk assessments
-
-

A Smarter Way to Manage Third-Party Risk
With Accountable's Third-Party Security Monitoring, you can streamline your vendor risk management and maintain compliance with confidence.
-
Track security risks across multiple third-party relationships
-
Ensure vendor compliance with up-to-date agreements and risk evaluations
-
Enhance security transparency by centralizing compliance documents
-
Proactively Secure Your Third-Party Network
By integrating third-party security monitoring into your compliance strategy, your organization can mitigate risks, enhance data security, and ensure regulatory compliance—all from one platform.
-
Automated tracking & monitoring for external business relationships
-
Risk questionnaire functionality to assess vendor security practices
-
E-signature support for seamless contract management
Features to power any privacy, security, and risk management program
Compliance
Employee Training
Vendor & Contract Management
Customer Trust
Security Risk Assessment
Identify & mitigate risks
Employee Dashboard
Monitor compliance progress
Vendor Management System
Manage vendor compliance
Incident Management
Report & resolve issues
Policy Management
Centralized policy control
HIPAA Training
Ensure HIPAA compliance
Third-Party Security Monitoring
Track vendor security
HIPAA Seal of Compliance
Verify HIPAA compliance
Data Inventory Management
Track & secure data
Security Awareness Training
Prevent cyber threats
Document Management System
Organize critical files
Privacy Center
Comply with DSAR laws
Policies & Procedures
Simplify compliance policies
Sexual Harassment Training
Foster workplace safety
BAA Management System
Simplify agreement tracking
Data Breach Monitoring
Detect & respond to breaches
Privacy Compliance Software
Automate privacy policies
Custom Training for Companies
Tailored employee learning
E-Signature
Secure digital signatures
Multiple Location Management
Centralized franchise compliance
Frequently Asked Questions
Can't find the answer you're looking for? Please reach out to our team.