HIPAA Compliance Checklist for 2021

The steps to compliance are not necessarily to be enacted in a specific order, but they are nonetheless required knowledge for a covered entity. Working toward compliance involves understanding the Security, Privacy and Enforcement Rules; having the necessary policies and procedures in place; running risk assessments; having disaster preparedness plans; implementing ongoing training; knowing how to collaborate with other affected parties; and executing business associate agreements.
Ready to simplify HIPAA compliance?
Join thousands of organizations that trust Accountable to manage their compliance needs.
Adopt the Correct Policies And Procedures
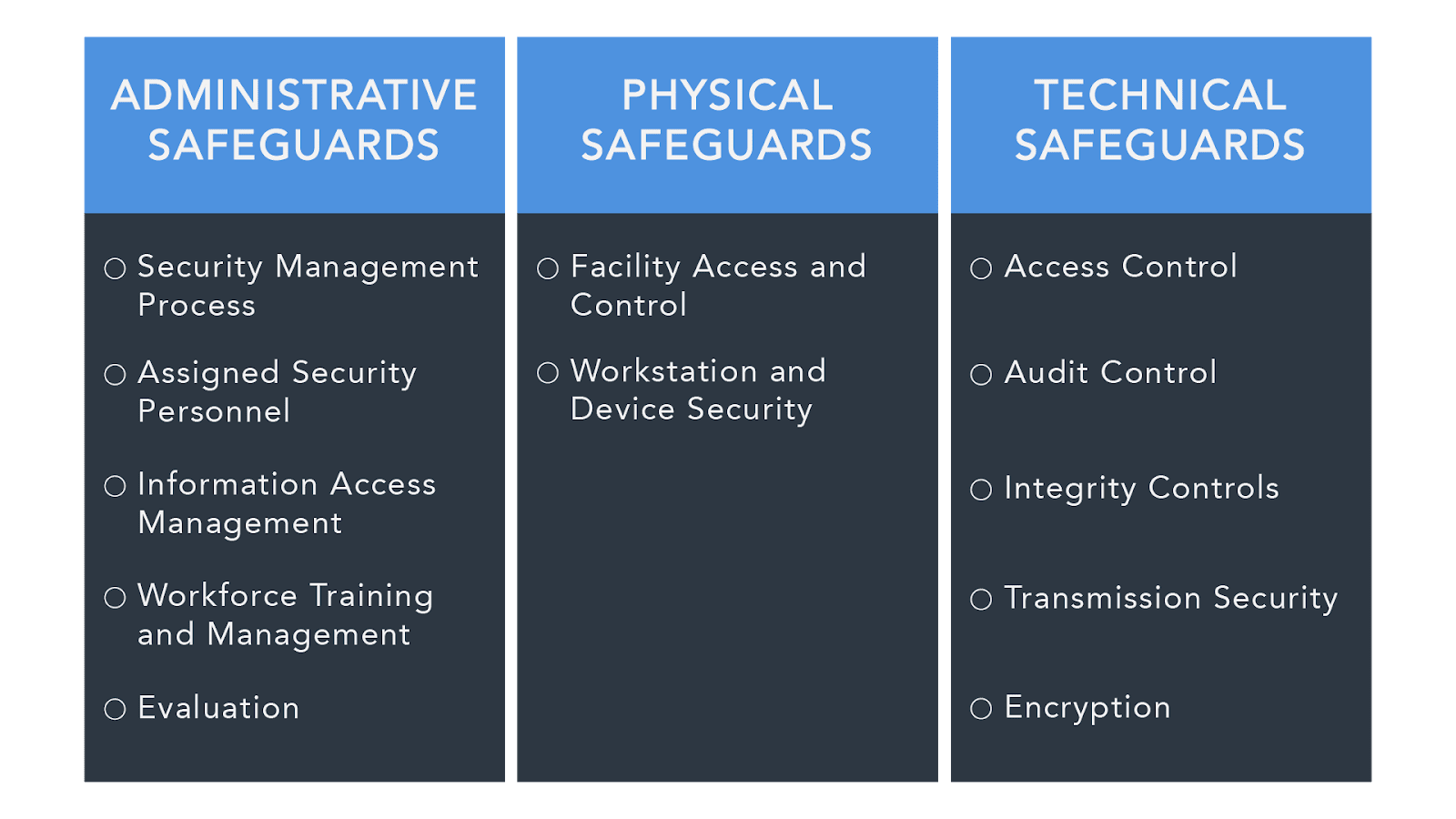
Under the HIPAA Security Rule, an organization is expected to have these three types of security measures in place to protect PHI:
- Administrative Safeguards - These safeguards are the policies and procedures designed to show how an entity complies with HIPAA on the administrative level.
- Covered entities must have a written list of privacy procedures and select a privacy officer, who will be responsible for implementing these procedures.
- In the case of management oversight, there should be a procedure in place for a buy-in to compliance, as dictated by the documented security controls.
- Procedures should lay out everyone who has access to Electronic Protected Health Information (EPHI) as a necessary part of their job.
- The procedures should also clarify authorization, establishment, modification, and termination, when it comes to PHI.
- There must be evidence of an ongoing training program with regard to those handling PHI.
- Covered entities must make sure all businesses with which they deal also comply by the necessary safeguards (through contracts), as well as making sure those parties only deal with other HIPAA-compliant entities.
- There must be a proven contingency plan in the case of emergencies. Covered entities must back up their data and provide evidence of a disaster recovery procedure. The plan should be continually updated to reflect ongoing data prioritization, system failures, security assessments, etc.
- There should be regular, internal, documented audits within covered entities.
- There must be a plan in place for responding to any security breach that might arise during an internal audit, or simply during day-to-day procedure.

2. Physical Safeguards - Physical safeguards protect the actual physical process of handling information and data.
- The introduction and disposal of hardware and software over open networks must be carefully monitored.
- All equipment containing any sort of PHI must be carefully monitored, with restricted access.
- Only authorized individuals may have access to hardware and software.
- There must be facility security plans in place, up-to-date maintenance records, and a sign-in/escort process for every visitor on the premises.
- Workstations should be treated appropriately, with information not visible in high-traffic areas.
- All contractors must also be aware of and comply with these physical safeguards.

3. Technical Safeguards - These safeguards refer specifically to the sharing of communications electronically in order to ensure they cannot be intercepted by outside parties.
- Systems with PHI must be secure against intrusion. When sharing information over networks, information must be encrypted.
- Entities must ensure data has not been tampered with.
- Further technical safeguards may be used to protect authentication.
- Covered entities must be certain of the authenticity of those with which they communicate.
- Covered entities must provide documentation of HIPAA practices so the government may determine compliance (see below for more information).
- The documentation of IT should incorporate a record of configuration settings on the network.
- Risk analysis and risk management programs are mandatory and must be available through documentation.
For medical practices, preparing for an audit involves being able to provide the following upon request:
- Having all the proper and aforementioned documentation on hand.
- Proof that the EHR system in place for meaningful use is certified.
- Documentation that all data is correct.
- Proof that a security risk assessment took place and physical evidence of a corrective action plan.
Running A Risk Assessment
Here is a possible scenario for running a Risk Assessment for your company:
- Determine the scope of analysis (as it extends to material contained on electronic devices, for instance).
- Aggregate data on Electronic Protected Health Information (EPHI) by reviewing past and current projects; reviewing all documentation; conducting interviews; and incorporating other means of data collection. Then, all accumulated data must also be documented.
- Identify and document all potential threats and vulnerabilities to the covered entity. Whether or not a threat is enough to exploit a vulnerability determines whether it would be considered a risk.
- Make an assessment of present security measures, including those which apply both electronically and physically. Document these as well.
- Determine the likelihood of the threat actually happening (the OCR provides a tiered system) .
- Determine the possible impact of the threat (the OCR has a checklist).
- Determine actual level of risk.
- Identify measures to manage risk.
For a similar list of steps for executing risk management, check the OCR's website.
Have A Disaster Preparation Plan
Having a disaster preparation plan is a crucial part of running a HIPAA compliant business. However, you might not know where to start when it comes to emergency planning.
Here are some websites that contain federally-developed emergency preparedness tools:
1. The Office for Civil Rights (OCR) provides the Department of Health and Human Services (HHS)'s primary information for helping with emergency preparedness as well as disaster recovery. Here you can find planning documents and links to other agencies that can also be of assistance.
2. The Agency for Healthcare Research and Quality (AHRQ) also has links to tools and resources for emergency and recovery planning.
3. The government also provides a decision tool to help you decide when information disclosure is acceptable in the case of an emergency.
Ongoing Training Programs
Ongoing training programs are a necessary component of HIPAA compliant entities. These programs are especially important as rules and guidelines can sometimes change quickly and covered entities need to safeguard themselves against possible security breaches.
HIPAA dictates that privacy and security training continue for employees and that "employees, volunteers, trainees, and other persons whose conduct in the performance of work for a covered entity [are] under the direct control of such entity, whether or not they are paid by the covered entity."
Not only must all members of the workforce involved with PHI be trained in the first place, staff must be retrained whenever there is a change in the organization's rules, policies, and/or procedures.
Entities should also make sure their business associates have continuing training programs as well. All businesses are able to contact their regional HHS offices for guidance and information on ongoing training for employees and associates.
More information on ongoing training is available on the American Health Information Management Association (AHIMA)'s website.
Executing Business Associate Agreements
A business associate is an individual or business that engages/performs duties with or for a separate covered entity.
As a covered entity, you must always make sure that any other party with which you are collaborating is not only HIPAA compliant itself, but that all of its other associates are also HIPAA compliant. Entering into contracts is the primary means of holding another party accountable for its actions.

Business associates enter into contracts to safeguard patient's protected health information. These contracts also limit and dictate the appropriateness of disclosing information in various scenarios.
There are ten official rules relating to business associate contracts, revolving around information disclosure. The official guidelines and a sample business associate agreement form can be found on the OCR's website.
Table of Contents
Ready to simplify HIPAA compliance?
Join thousands of organizations that trust Accountable to manage their compliance needs.




