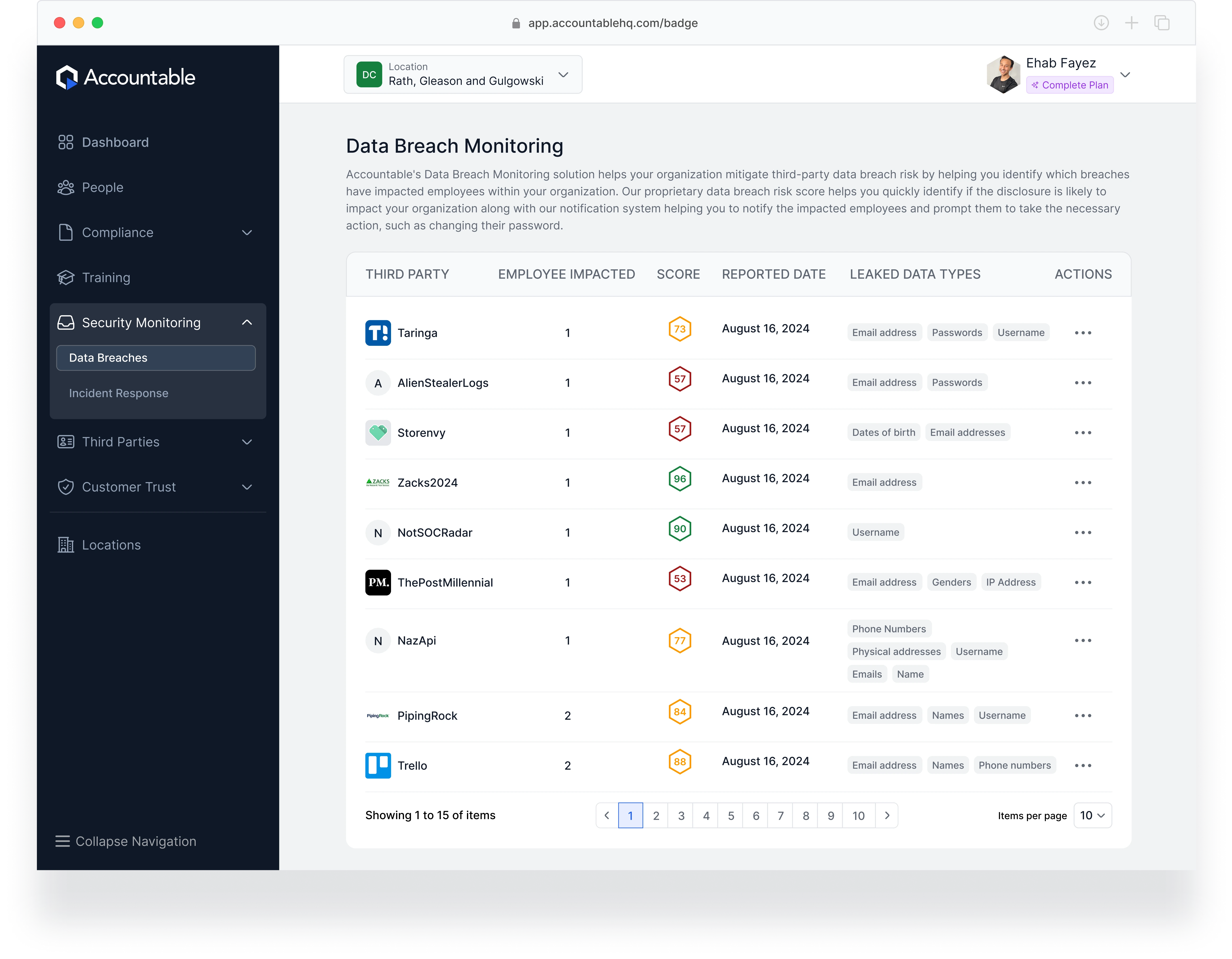
Data Breach Monitoring
Cyber threats and third-party data breaches put businesses at constant risk. Accountable's Data Breach Monitoring solution helps organizations identify, assess, and respond to security incidents that could impact employees and sensitive data.






-
Automated Data Breach Detection & Risk Scoring
With Accountable's Data Breach Monitoring, your organization can:
-
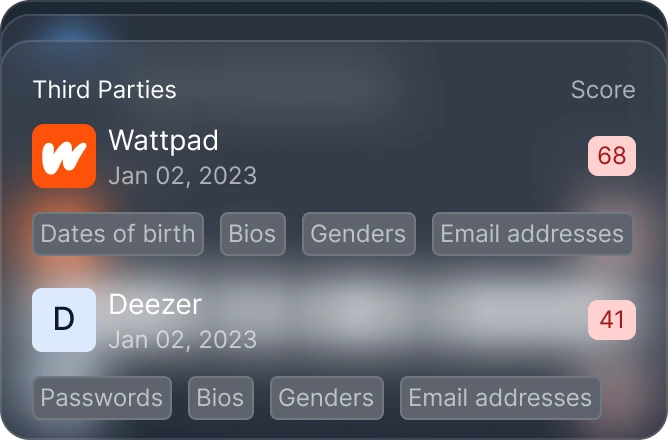
Detect third-party breaches affecting employee accounts in real time
-
Assess risk levels with a proprietary data breach risk score
-
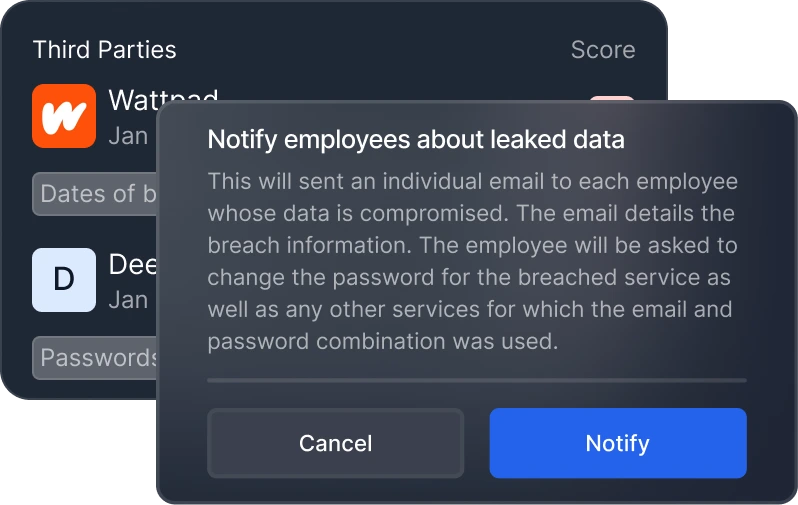
Automatically notify impacted employees and prompt necessary actions
-
-
Minimize Risk & Strengthen Security
-
Continuous monitoring – Track data breaches from external services linked to your organization
-
Proactive security alerts – Get notified when an employee's credentials are compromised
-
Automated response system – Prompt employees to take action, such as changing their passwords
-
Why Choose Accountable's Data Breach Monitoring?
With Accountable's Data Breach Monitoring, your organization can stay ahead of cyber threats, mitigate third-party risks, and protect sensitive data—all from a single, automated platform.
-
Puts breach monitoring on autopilot to reduce manual oversight
-
Enhances organizational security by responding to risks faster
-
Helps meet compliance requirements by ensuring prompt breach notifications
Features to power any privacy, security, and risk management program
Compliance
Security Risk Assessment
Identify & mitigate risks
Employee Dashboard
Monitor compliance progress
Policy Management
Centralized policy control
Data Inventory Management
Track & secure data
Policies & Procedures
Simplify compliance policies
Privacy Compliance Software
Automate privacy policies
Employee Training
HIPAA Training
Ensure HIPAA compliance
Security Awareness Training
Prevent cyber threats
Sexual Harassment Training
Foster workplace safety
Fraud, Waste, & Abuse Training
Learn best practices
Bloodborne Pathogens Training
Prevent exposure
Custom Training for Companies
Tailored employee learning
Frequently Asked Questions
Can't find the answer you're looking for? Please reach out to our team.